Many contractors think paperwork and policy updates are enough to satisfy compliance, but technical gaps often tell another story. CMMC level 2 compliance requires more than documenting procedures—it demands proof that security controls work against real threats. That’s where technical testing can reveal whether protections stand firm or if unseen weaknesses still put federal data at risk.
Comprehensive vulnerability illumination across all systems
Technical testing provides a wide lens across every connected device, server, and endpoint. Instead of relying solely on checklists, vulnerability scans expose misconfigurations, outdated software, and overlooked entry points that attackers could exploit. Meeting CMMC compliance requirements demands this type of visibility, because even small oversights can compromise controlled unclassified information.
Unlike surface-level reviews, vulnerability testing dives deeper into hidden layers of infrastructure. This illumination helps contractors demonstrate to a C3PAO that their security program addresses both visible and concealed risks. For companies preparing for CMMC level 2 compliance, this process confirms readiness while also strengthening practices that extend beyond compliance audits.
Validation of real-world attack vectors against implemented controls
An assessment of policies is not enough without testing how those policies perform under simulated threat conditions. Penetration testing validates whether implemented controls actually repel the same methods adversaries would attempt in the real world. This includes phishing simulations, lateral movement attempts, and privilege escalation tactics.
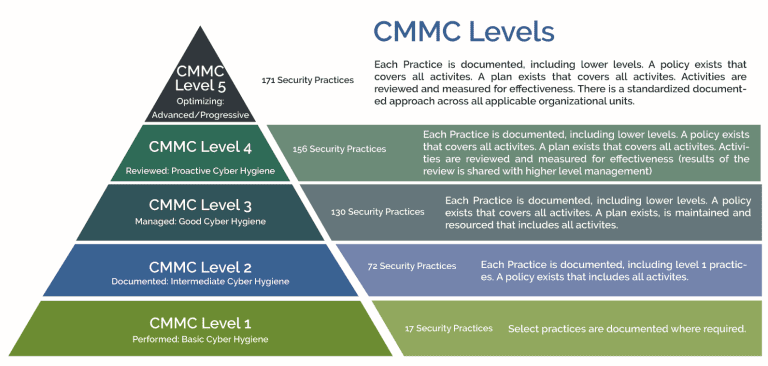
By validating defenses this way, contractors align their security posture with the intent of CMMC level 2 requirements rather than just the written word. It proves to both assessors and stakeholders that existing protections are not theoretical but demonstrably effective. This makes a stronger case for CMMC level 2 compliance than documentation alone ever could.
Ensuring alignment of defenses with NIST 800-171 technical mandates
Since CMMC level 2 requirements map directly to NIST 800-171, technical testing acts as a translator between compliance language and operational performance. Each mandate—such as encryption standards or incident response readiness—can be tested for measurable proof of effectiveness.
A personal review of these controls may overlook implementation flaws, but structured testing ties compliance requirements to observable outcomes. This alignment provides a clear demonstration during C3PAO audits that technical safeguards are functioning as NIST 800-171 intends. For contractors, it bridges the gap between compliance paperwork and actual defensive capability.
Continuous stress on internal and external perimeter resilience
Attackers never stop probing for weaknesses, which means perimeter defenses cannot be static. Regular stress testing of firewalls, intrusion detection systems, and external-facing assets ensures resilience against both automated scans and targeted attempts. Internal networks also need equal attention, as insider threats or compromised devices can bypass perimeter defenses altogether.
CMMC compliance requirements emphasize layered protection, and this is where stress testing proves essential. By continuously challenging both internal and external perimeters, contractors meet not only CMMC level 1 requirements for basic safeguarding but also the more rigorous standards of CMMC level 2 compliance.
Measurement of control efficacy under simulated threat pressure
Controls that appear strong on paper may falter under active pressure. Simulated attacks measure whether security mechanisms respond as intended under hostile conditions. Testing under this lens includes evaluating intrusion prevention systems, endpoint detection tools, and automated response workflows.
The measurement of control efficacy serves as both validation and a guide for improvement. If a response tool delays detection or fails to quarantine malicious activity, technical testing exposes the gap before an adversary exploits it. This step plays a vital role in preparing organizations for CMMC RPO recommendations or formal assessments.
Detection of latent weak links in authentication and access layers
Authentication remains one of the most targeted layers in any environment. Technical testing identifies weak password policies, flawed multifactor authentication setups, and improperly configured access controls. These areas often create the silent entry points attackers rely on to bypass stronger perimeter defenses.
Because CMMC level 2 requirements focus heavily on controlled access to sensitive data, detection of weak links ensures compliance readiness. By addressing these vulnerabilities, contractors strengthen their position before presenting to a C3PAO and demonstrate adherence beyond CMMC level 1 requirements.
Affirmation that logging, monitoring, and alerting work as expected
CMMC compliance requirements expect contractors to maintain robust logging, monitoring, and alerting functions. However, the presence of monitoring tools does not guarantee they work as intended. Technical testing affirms whether alerts trigger in real time, logs capture relevant activity, and monitoring systems integrate properly with incident response workflows.
Affirmation through testing is invaluable during a CMMC level 2 compliance review. It gives assessors clear evidence that systems not only exist but perform effectively. Contractors that validate these mechanisms also reduce the risk of prolonged detection gaps during actual intrusions.
Correlation of test findings with corrective action planning
Technical testing is only half of the equation. The other half is correlating results with a corrective action plan that aligns with CMMC RPO guidance. Findings reveal where gaps exist, but structured planning ensures those weaknesses are addressed in order of priority and tied back to compliance requirements.
Corrective action planning builds a roadmap that demonstrates to a C3PAO both transparency and accountability. This correlation shows a commitment to continuous improvement, a key expectation under CMMC level 2 requirements. Contractors who adopt this cycle of testing and correction establish resilience while achieving compliance with lasting impact.